




It’s that time of year again! When we enjoy a pumpkin spice latte with an extra helping of security. Because those free wifi hotspots come at a price.
You’ll be seeing lots of friendly reminders online this month, and we can all use a refresher on how to “keep it secret, keep it safe”. Gandalf was wise indeed!
So today is a quick review of easy wins for you to get started 😃
1. Protect your passwords. Don’t share them. Don’t write them on sticky notes or where others can see them. And make them long and strong: go for 16 characters with numbers and special characters
2. Use a VPN. Virtual private networks are not all powerful but they’ll shield your sensitive data from public access
3. Think before you click. Seriously! Scammers are rampant and creative. Don’t click on attachments from strangers or unexpected links from familiar names. Stranger danger ⚠️
4. Update all the things: Windows, Chrome, iOS, Mac etc. Any software and operating systems, but even your printer or smart TV. Those security updates patch vulnerabilities in the code that can expose you through your unpatched devices
5. Bug off! Use antivirus and anti malware products to help keep watch over your systems and prompt you if something seems suspect
That’s a great start for now and these are tips you can share with family and friends to keep them safe too. Thanks for reading 😊
It’s been a year away, a year of many things. We are all finding our way forward, having to accept whatever this new pandemic reality is. Not post-pandemic because it is not over but has now been deemed “endemic” – here to stay.
Yes, I have had Covid despite all precautions and efforts. Yes, long covid is real and I am still regaining my lost energy and focus. And then there is burnout, which you only realize when the damage is done and there’s no quick fix. There has been time off, time away to restore and just breathe. There have been virtual talks and in-person talks after a long time away. Because learning is a joy and sharing what we learn even more so.
I have taken risks to move forward which also meant moving away. Cities in pandemic lockdown can become prisons, shutting us down from the inside. My new space gives me sky, trees, distant hills and constant beauty to drink in daily. And I am grateful.
2022 has been a year of returns and welcome backs, the elation tempered by caution and hesitation because of what we know and the risks we choose. We returned en masse to Hacker Summer Camp, a reunion long-awaited and carefully considered. We were fully vaxed, constantly masked, testing daily and limiting our exposure, foregoing restaurants and parties based on our risk assessment. We made dozens of air filters for our conference spaces and used monitors. It was what we could do to do what we love and it did work for us at that point in time. But Covid has taught us there are no guarantees.

Never say never. We are living in a time of massive change, history moving us through a series of events we knew would be coming but yet caught us unprepared. Putin’s invasion of Ukraine, natural disasters of epic proportions, a global food shortage, an impending energy crisis as winter looms, a new pandemic while entire cities in China locked down tens of millions for ongoing Covid, and the looming threat of a global economic downturn. We now must question what we thought against what we are observing, and accept that we must change our approach. Old solutions aren’t working for new problems because things have changed. We have changed. There is no going back.
I am so happy to be presenting at Hackfest once again. This year will be virtual, with the usual excellent selection of cutting edge talks and trainings – you should really check them out. Hackfest is also known for its CTF, and features a beginner one. And of course there are villages and sponsors to visit!
I’ll be presenting at 2:30 EDT Friday November 19, 2021. “Signed, Sealed, Delivered: Abusing Trust in Software Supply Chain Attacks”. Because that’s been a thing this year 😉 I’ve attached my slide deck below. Hope you can join the fun!

There were donuts and APTs involved, just not at the same time 😉


The events were well done, with excellent talks and my sincere appreciation to the volunteers who made it all happen and were super helpful. I was so happy, so honored to have been invited to speak at each of these villages virtually this year, and to have been involved in Defcon this year. I miss the live conference experience and especially Hacker Summer Camp ❤


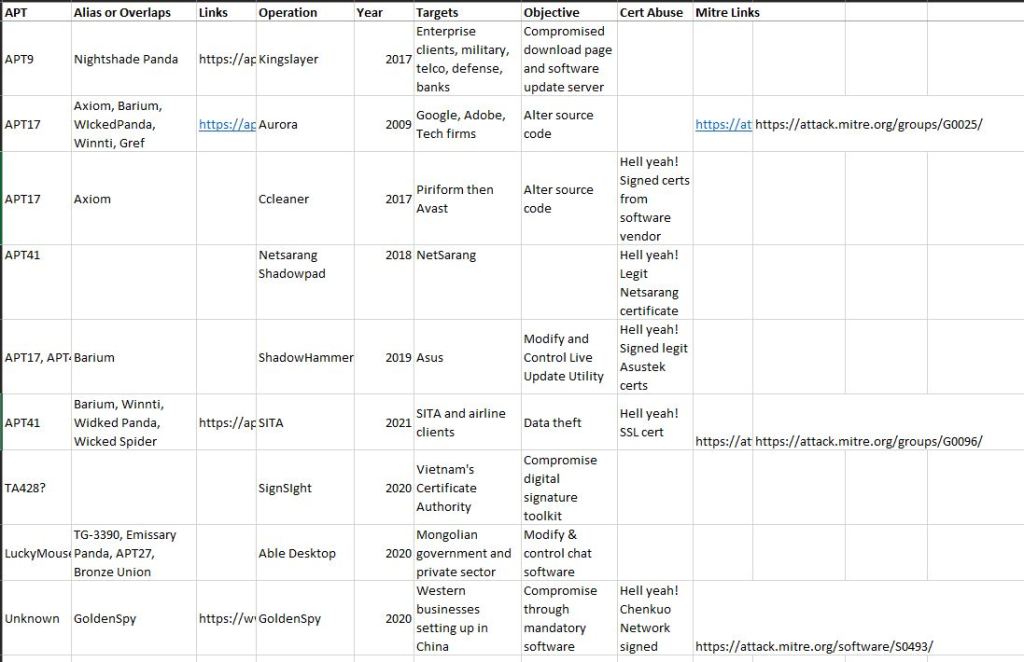
This is to accompany my talk at Defcon 29 Adversary Village (ZOMG really thrilled to say that). It’s a work in progress. Chinese APTs are wonderfully, frustratingly complex entities. There’s a lot of overlap, sharing of tools, techniques, malware. Of note was certificate abuse across the board. And several companies with striking resemblance to SolarWInds offering trusted high level network management to major organizations and government globally. It’s happened before, it will happen again.
So take this as a starting point. Rather than reinvent the wheel, check the links in the file for download to Thaicert’s excellent site on Threat actors, and of course the relevant pages from MITRE. I’ll revise and refresh this as I dig deeper. These attacks are only going up.

Spark a Journey! This is the week! Friday July 16 and Saturday July 17. This year’s event will be virtual again, building off success and lessons learned from last year.
As the website states, TDI is a diversity-driven conference committed to helping all underrepresented genders, sexualities, races and cultures in Information Security.
The theme for 2021 is “Spark A Journey” to celebrate that force, that spark within each of us that can lead to many ways we inspire and drive change. The beautiful stylized images of the paper cranes by the wonderful @1dark1 represent metamorphosis, a symbolic re-emergence after the many long months of pandemic confinement and isolation. It’s a hopeful, empowering message we all need just now.
This year’s event will have multiple speaker tracks, fully expanded villages and workshops and a women-led Capture the Flag event. Tickets are available and so affordable! Get yours here and come join us: https://hopin.com/events/2021-diana-initative



To be honest and cliche, today feels like the first day or the rest of my life. There are so many still in that dark place of despair and isolation but this second dose represents a lifeline up and out, to brighter days and all the possibilities. Hang onto your hope