BANKS
After 2016’s massive financial attacks and heists, and the return of Carbanak, financial organizations need to get their houses in order to face the year ahead. And it isn’t just the gold or currency that holds value in the vault. It’s all. That. Data. Those mainframes are no longer as segregated as they once were. And banks are more at risk of Advanced Persistent Threats and targeted attacks. Recommendations are to train everyone on security practices and awareness. Then, make sure controls are in place and that people are aware of them. Finally, make sure that all outside parties, or trusted partners, understand and adhere to these rules to maximize security.
Polish Bank Heists (February 14, 2017): The recent series of targeted malware attacks against Polish banks is part of a wider campaign that has gone after financial institutions in over 30 countries. According to researchers from both BAE Systems and Symantec, the malware used in Poland can be linked to similar attacks around the globe, and there are marked similarities to tools used by the cybercrime group Lazarus, although no confirmation has been made. Targets were led to compromised sites of interest to them, watering holes, which were malicious sites that injected code and directed the targets to a customized exploit kit. This kit contained exploits against known vulnerabilities in Flash Player and Silverlight. What’s interesting is that the exploits were only activated for certain visitors: those with IP addresses from specific ranges. This is when a standard attack is elevated to sophistication at the APT level. Per Symantec, “The IP addresses belong to 104 different organizations located in 31 different countries … The vast majority of these organizations are banks, with a small number of telecoms and internet firms on the list.” 15 of these are from the US. The infection downloaded enables recon on the compromised system. Again, this tool is similar to those used in past by the Lazarus group.
Stux for Banks (February 9, 2017): Bad as Carbanak is, Stuxnet is worse. Kaspersky will be releasing all the details in April at their annual summit but for now, we can go with this: that nasty new fileless malware hitting banks is Duqu 2.0, which Kaspersky found on it corporate network in 2014, but only after it went undetected for 6 months because it lives almost completely in the memory of the computers. Duqu 2.0 is derived from Stuxnet. The malware renames itself when an infected computer is rebooted so digital forensics has a tough time finding traces. The calling card seems to be the unusual embedding of PowerShell into the registry to download Meterpreter. Duqu 2.0 is derived from Stuxnet. Researchers aren’t saying how the malware spreads.
Major Banking Insecurities (February 6, 2017): You may have noticed more reports on cyber incidents and banks. Yes, it’s a definite upswing. This may be part of the reason. According to Capgemini, one in five bank execs are “highly confident” in their ability to detect a breach, never mind defend themselves against it. Yet “83% of consumers believe their banks are secure from cyber attack”. They put their trust, and their money, in these venerable institutions. How about this? One in four banks report they’ve been attacked, but only 3% of consumers believe their bank has suffered a breach. Never mind the money. How about the data? Survey shows that 71% of banks don’t have a solid security strategy in place, nor do they have adequate data privacy practices. The numbers are not good. Roughly 40% of banking and insurance companies have automated security intelligence capabilities for proactive threat detection. As the saying goes “In God we trust”. Not so much banks.
Lurk Malware (February 10, 2017): From Russia with love. Lurk malware was actively involved by a Russain cybercrime operation. The gang stole $28.9 million from customer accounts starting in 2013. Other countries were also targeted. When the gang went after another $39.1 million by issuing false payment instructions (does that sound familiar – SWIFT?) they were blocked. Lurk first appeared in 2011 and was used in click fraud. It was revamped to exploit weaknesses in bank security, and was used along with the Angler exploit kit to infect endpoints. Interesting point: the banks learned what was being used and adjusted their defences accordingly. So the investment by the crime gang became costly overhead. Several Lurk members were arrested mid-2016 around when the Angler exploit kit disappeared. Cisco Talos team reports the Lurk gang was also involved in the Necurs botnet which distributed Locky ransomware and Dridex banking malware.
Is Carbanak Back? (February 8, 2017): Carbanak is a big deal. Given its success to the tune of $1 billion in bank heists, it’s a very big deal. And we’ve been watching it pivot into the hospitality industry, where low hanging fruit literally is the reason. However, Carbanak is too established in the finance realm to stay dormant. We’ve also covered the increase in attacks on banks globally, leveraging fileless malware, and common, accepted tools like PowerShell and Metasploit most recently. This is not signature based malware that can be referenced and detected. According to Kaspersky, 140 enterprises in 40 countries have been hit. For those of us in DFIR:
“ memory forensics is becoming critical to the analysis of malware and its functions. In these particular incidents, the attackers used every conceivable anti-forensic technique; demonstrating how no malware files are needed for the successful exfiltration of data from a network, and how the use of legitimate and open source utilities makes attribution almost impossible.”
Details show similarities to the Carbanak gang, who used spear-phishing and backdoors to manipulate access to banking networks globally, including SWIFT. This is such a big deal I am giving you two infographics on it. And I say where there is smoke …

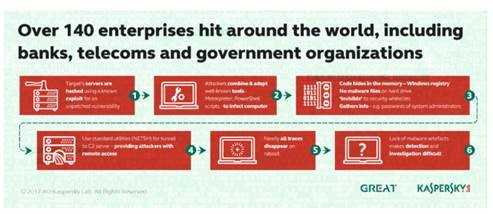
Attack of the Fileless Malware (February 8, 2017): This is a heads up. Fileless malware has hit banks around the globe. The malware lives solely I the memory of compromised systems, which is usually distinctive of APTs and nationstate attacks. Think Stuxnet, gone public. Kaspersky Labs will be reporting that at least 140 banks have been infected by “malware that relies on the same in-memory design to remain nearly invisible”. But the infections are hard to identify so that number could well be more. Further complicating things is the use of legitimate and widely used sysadmin and security tools like Powershell, Metasploit and Mimikatz for malware injection. In a range of incidents, the common denominator seems to be embedding Powershell in the registry to download Meterpreter. From there, the attack is carried out using the native Windows utilities and syadmin tools.
Attacks on Polish Banks (February 6, 2017): We reported on this last Friday. Several polish banks have been attacked but not for money – for data. It has been confirmed the malware was on the Polish banking regulator site. And had been installed there by a foreign party for purposes of espionage, as the malware connected to foreign servers for exfil, recon and post exploitation activity.
After noticing unusual network activity, like traffic to “exotic” locations and encrypted executables that nobody knew of, and unauthorised files on key machines in the network, several commercial banks confirmed malware infections. Investigations are in their early stages, but there is a possibility infection stemmed from a tampered JS file from the webserver of the Polish financial sector regulatory body. The attack is not a quick hit and run but sophisticated: “the malware used in this attack has not been documented before. It uses some commercial packers and multiple obfuscation methods, has multiple stages, relies on encryption and at the moment of initial analysis was not recognised by available AV solutions. The final payload has the functionality of a regular RAT”.
Give us Your Data (January 31, 2017): Several polish banks have been attacked but not for money – for data. After noticing unusual network activity, like traffic to “exotic” locations and encrypted executables that nobody knew of, and unauthorised files on key machines in the network, several commercial banks confirmed malware infections. Investigations are in their early stages, but there is a possibility infection stemmed from a tampered JS file from the webserver of the Polish financial sector regulatory body. The attack is not a quick hit and run but sophisticated: “the malware used in this attack has not been documented before. It uses some commercial packers and multiple obfuscation methods, has multiple stages, relies on encryption and at the moment of initial analysis was not recognised by available AV solutions. The final payload has the functionality of a regular RAT”.
| (January 26, 2017): It’s not unusual to see exploits fade away, and then return with a new twist. Infact, it’s something we should be expecting and prepared for. Zeus Sphinx was identified in August 2016 when it attacked Brazilian banks. The activity seemed to die down. However, researchers with IBM X-Force report that the malware authors have been making consistent small code updates. Now, it appears a new campaign has commenced, targeting online bank users in Canada and Australia. These attacks are specific, 33 URLS identified for Canadian financial institutions. Notably credit unions which may have fewer defences in place and are attractive low-hanging fruit. Attackers are using the same attack servers from 2016 that deployed Zeus Citadel and Ramnit attacks. |
Lloyd’s Bank hit by DDoS attack (January 23, 2017): We’re just hearing about this now, but on January 11 the venerable Lloyd’s Bank of London was struck by a DDoS attack that lasted until Friday January 13th. Attackers tried to crash the Lloyd’s site, causing issues for customers and impacting some access to online banking. The bank did not lose money, nor data, nor was the impact significant. Law enforcement is investigating. http://news.softpedia.com/news/lloyds-bank-hit-with-ddos-attack-for-three-days-straight-reasons-yet-unknown-512114.shtml
SWIFT systems compromised in Indian Banks (January 16, 2017): News about other attacks on SWIFT partners has been trickling out since last year’s mega story about the Bangladesh bank heist. In this case, attacks were aimed at 3 government-owned banks in India. The attackers chose to create fake trade docs like letters of credit and guarantees. This is a change from compromising the SWIFT system itself to send fraudulent info on financial transactions. So far, no monetary losses or ransom demands have been reported in connection with the attacks. There is no answer yet as to how the compromises were made. The Reserve Bank of India has been advised, and are checking the trade documents they sent via SWIFT have matches. https://www.helpnetsecurity.com/2017/01/16/swift-systems-indian-banks-compromised/
Follow Up to the Bangladesh Bank Heist: Remember the attack that took $100 million dollars from the bank in Bangladesh early this year? Charges have been filed against 5 officials of RCBC bank and a former treasurer, Rau Tan who had “willfully ignored” suspicious activity. The Anti-money Laundering Council found the parties guilty “because they should have noticed something was wrong and intervened immediately.” Only $15 million has been recovered and returned. $2.7 million more has been frozen. The remainder has apparently changed hands several times and is somewhere in the Philippines casino industry. No other arrests have been made despite investigations by the FBI, Interpol, local police and authorities. The bulk of the blam in a recent report falls on Tan as being able to “enhance due diligence … convene the anti-money laundering committee” etc.
https://ca.news.yahoo.com/philippines-money-laundering-body-charges-bankers-ignoring-cyber-045625298–finance.html
Inpage Zero Day Used in Attacks Against Banks: Attacks against banks in the Middle East has been attributed to a zero day vulnerability in InPage publishing software, popular in the region. Kaspersky made the disclosure after numerous attempts to privately report the bug apparently went ignored. Kaspersky says “it’s possible a number of criminal or nation-state actors are using this exploit” based on the attacks it has recorded against banks and government agencies in Asia and Africa. The exploit spreads via phishing, and builds off several Office exploits. An interesting comparison is attacks against governments in South Korea via vulnerabilities in the Hangul Word Processor, which FireEye traced back to North Korea.
https://threatpost.com/inpage-zero-day-used-in-attacks-against-banks/122112/
Hacker Group COBALT hits ATMs Across Europe: We know ATMs are risky business. This year, there have been some major attacks and coverage on these as a favoured target. The latest siege, Cobalt, covers a wide swath across the UK, Spain, Russia, Romania, the Netherlands, much of Eastern Europe and Malaysia. According to Group IB researchers, a large number of machines are attacked at once, and Cobalt appears to be linked to cybercrime syndicate Buhtrap. The malware used causes infected machines to spit out cash in an attacks known as “jackpotting”. Noteworthy is how this is being described as “the new model of organized crime”. Earlier this month the FBI issued warnings to US banks following those ATM heists, and taking into account the attacks in Taiwan and Thailand, when thieves grabbed over 260,000 pounds from Thailand’s Government savings bank and $2.5 million from Taiwan. The world’s two largest ATM manufacturers, NCR and Diebold Nixdorf, are working to manage the threat. More heists are expected.
http://www.ibtimes.co.uk/hacker-group-cobalt-hits-atms-across-europe-1592748?utm_content=buffer2bca1&utm_medium=social&utm_source=twitter.com&utm_campaign=bufferhttps://cdn.ampproject.org/c/thehackernews.com/2016/11/atm-hack-malware.html?amp=1
Lessons From the TESCO Bank Attack: 2016 brought banking insecurities to the forefront via massive heists, new Trojans, ATM attacks and shutdowns. The recent attack on Tesco online bank in the UK, which is a good parallel to our PC Bank here in Canada, serves as a reminder that banks, and all business in general, need to know their environments. That means having controls in place to alert on changes to key files and configurations. Because as humans, we are fallible. Mistakes will be made. And that is what the attackers are literally “banking on”. File monitoring integrity and Configuration Management Security ensure that if and when changes are made, they are valid and validated. This blog is a good run through of the how and why.
https://www.tripwire.com/state-of-security/security-data-protection/technology-helped-prevent-tesco-bank-breach/
Russian Banks Latest Target in DDoS Attacks: The attacks against major Russian banks last week should keep us mindful of where DDoS is heading. They were powered by compromised IoT devices, according to an unnamed Russian Central Bank official, and took the banks down for extended periods of time. At the root is the ongoing message around password management and removing default passwords from both consumer and industrial devices.
http://www.theregister.co.uk/2016/11/11/russian_banks_ddos/
