I’ve been known to exaggerate but trust me when I say that this latest security threat is so big it’s off the charts. Literally. It was rated as a 10 out of 10 by the National Vulnerability Database. A an official advisory was issued by the Department of Homeland Security, and they don’t just hand those out freely. While this won’t ruin your life the way getting caught in a Home Depot style data breach could, it puts at risk almost every device that connects to the internet. Since our world has become the Internet of Things (see previous post for neat-o chart), that means a lot of risk. So here is what you need to know, and why.
Bash stands for Bourne-Again Shell, a very common program used to run line commands in operating systems like Linux, Unix, Mac OS X. The shell is where we interface with or control the operating systems, and these run pretty much everything we connect to or rely on for connectivity and our “smart” devices. Per trend Micro, “Linux powers over half the servers on the Internet, Android phones and the majority of devices in the IoT (Internet of things).”
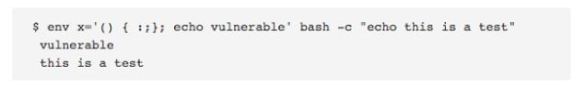
The problem is a vulnerability that lets an attacker easily access and make changes to the CGI script written in Bash, those commands that are issued to the operating system. And no credentials are required. As security experts Kaspersky put it “This vulnerability is unique, because it’s extremely easy to exploit and the impact is incredibly severe.” This doesn’t just impact servers. It impacts devices connecting to these servers through the internet: wireless access points, routers, smart fridges, video cams, webcams, even light bulbs. You can patch a server. It’s not so easy to patch a fridge.
And this is where the other shoe drops. In his article for Fast Company, Chris Gayomali explains how this vulnerability “also affects Bash versions stretching back at least 25 years, meaning, when or if a patch rolls out, there are a number of older electronics that won’t be getting a firmware update.” The obvious solution has been to issue patches, but the issue is if and when everything affected will have patches available. The problem may have the worst impact on major institutions, like banks and hospitals, where change happens slowly and systems have been laboriously put together over time. According to Patrick Thomas, a security consultant at Neophasis labs, “their most venerable systems are also their most vulnerable.”
So what do we do, now that we know? Systems experts are testing for and patching webservers as I write this. Hopefully, our Internet service providers have been successful. As have those companies who host our websites. Here is some excellent advice from Mark Nunnikhoven at Trend Micro:
1. End users should watch for patch updates or alerts for their Android phones, Macs, or other devices.
2. As a customer of a hosted service, like a website, contact the host directly and ask them if they have patched the vulnerability. If not, why not?
For those running a system that uses Linux, or an Apache webserver, this article by Kaspersky Labs recommends updating Bash and outlines helpful ways to test for the vulnerability: http://securelist.com/blog/research/66673/bash-cve-2014-6271-vulnerability-qa-2/.
Truth is, there’s really not a lot you can do to fix the #bashbug. But you can find ways to stay informed, ask questions (from service providers or friendly folks like me), and follow the practical advice in my earlier posts about protecting yourself. And that is how you can be your best defence against an unexpected offence like this. Welcome to Fortress Security.